For those who are new to school, new to the field of Information Technology – IT, to those who work … they must have heard many times VPN, or virtual private networks, virtual personal networks … So what is VPN, what are the pros and cons of VPN? Let’s discuss the definition of VPN, how to apply this model, system at work.
Contents
What is a VPN?
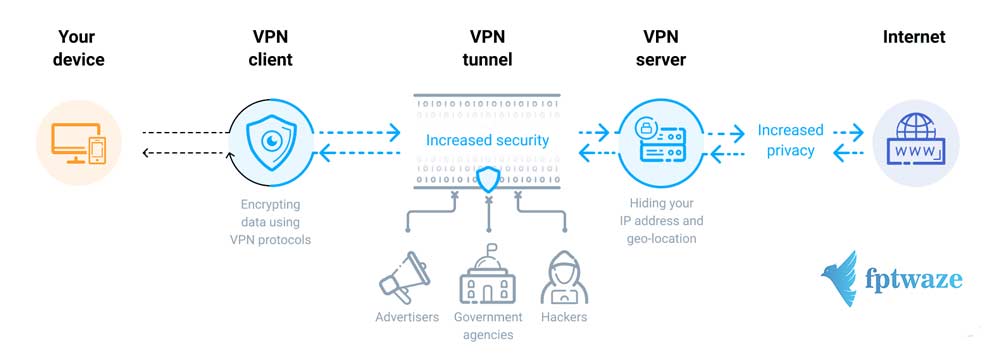
VPN is a virtual private network, which is a network technology that helps create a secure network connection when participating in a public network such as the Internet or a private network owned by a service provider. Large corporations, educational institutions, and government agencies use VPN technology to allow remote users to securely connect to their own networks.
How to VPN works
VPN system can connect many different sites, based on region, geographical area … as the Wide Area Network (WAN) standard. Besides, VPN are also used to “diffuse”, expanding Intranet models to transmit information and data better. For example, schools have to use VPN to connect between campuses (or between branches and headquarters) together.
If you want to connect to a VPN system, each account must be authentic (Username and Password required). These account authentication information is used to grant access through 1 data – Personal Identification Number (PIN), which usually only works for a certain period of time (30 seconds or 1 minute).
When connecting a computer or another device such as a phone, tablet to a VPN, the computer works just like it is on the same in-network as the VPN. All traffic on the network is sent over a secure connection to the VPN. This helps you securely access in-house network resources even when you’re far away.
You can also use the Internet just like you’re in the location of a VPN, which offers some benefits of using public WiFi or accessing a blocked, geographically limited website.
When browsing with a VPN, the computer contacts the website through an encrypted VPN connection. All requests, information, data exchanged between you and the website will be transmitted in a secure connection. If you use a VPN in the UNITED States to access Netflix, Netflix will see your connection coming from the United States.
While it sounds pretty simple, in fact a VPN is used to do a lot of things:
- Access to a business network while away: VPN are often used by business people to access their business networks, including all resources on the local network, while on the road, traveling,… Resources in the in-network do not need to be in direct contact with the Internet, thereby increasing security.
- Access your home network, even if you’re not at home: You can set up your own VPN to access when you’re not at home. This will allow remote access to Windows through the Internet, using files shared in the in-network, playing computer games over the Internet just like being in the same LAN.
- Browse anonymously: If you are using public WiFi, browsing on non-https sites, the safety of data exchanged in the network will be vulnerable. If you want to hide your browsing activity so that the data is more secure then you should connect to a VPN. All information transmitted over the network will now be encrypted.
- Access to websites that are blocked from geography, bypass Internet censorship, bypass firewalls,…
- Download files: Downloading BitTorrent on a VPN will help speed up file downloads. This also helps with traffic that your ISP can get in the way of.
Protocols in VPN
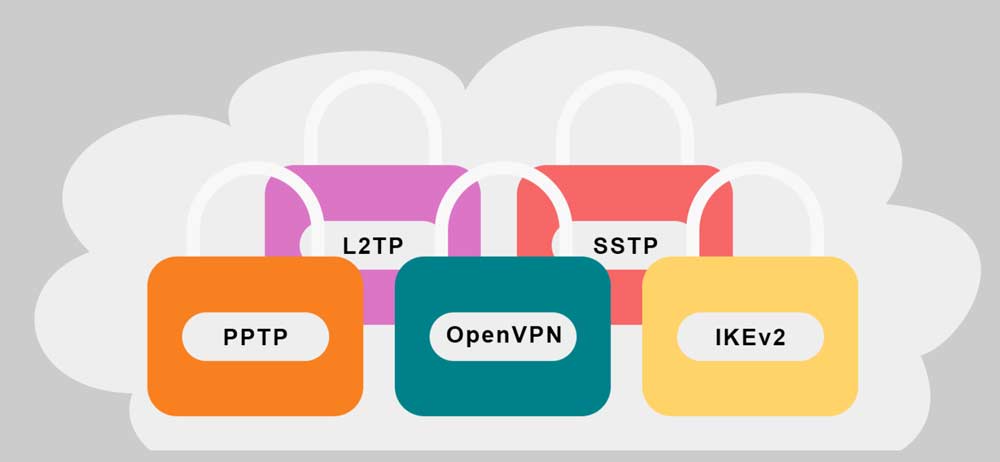
VPN products often have a variety of convenience, efficiency, and security. If security is a top concern, then an organization needs to pay attention to the protocols that a VPN supports. Some widely used protocols have concerns, while others offer the most advanced security. The best protocols today are OpenVPN and IKEv2.
VPN protocols
The essence of a VPN protocol is a set of protocols. There are a number of functions that every VPN must solve:
Tunnelling: The basic function of a VPN is to distribute packets from one point to another without exposing them to anyone on the line. To do this, the VPN packages all the data in a format that both the client and the server understand. The data sender puts it in tunnelling format and the recipient extracts to get the information.
Encryption: Tunnelling does not provide protection. Anyone can extract the data. Data also needs to be encrypted on the line. The recipient will know how to decrypt data from a certain sender.
Authentication: For security, a VPN must confirm the identity of any client trying to “communicate” with it. The client needs to confirm that it has reached the correct intended server.
Session management: Once the user is authentic, the VPN needs to maintain the session so that the client can continue to “communicate” with it for a period of time.
Generally, VPN protocols treat tunneling, authentication, and session management as a package. Weaknesses in any function are potential security flaws in the protocol. Encryption is a specialization, it’s also very difficult, so instead of trying to create a new one, VPN often use a combination of multiple reliable encryption protocols. Here are the popular VPN protocols and their weak strength.
Weak protocols
Point-To-Point Tunneling Protocol (PPTP)
The oldest protocol still in use is the PPTP (Point-to-Point Tunneling Protocol). PPTP was first used in 1995. PPTP does not specify an encryption protocol but may use some protocols such as the powerful MPPE-128. The lack of strong protocol standardization is a risk, as it can only use the strongest encryption standard that both sides support. If one side only supports weaker standards, the connection must use weaker encryption than the user expected.

However, the real problem with PPTP is the authentication process. PPTP uses the MS-CHAP protocol, which can be easily cracked in the current period. An attacker can log on and impersonate an authorized user.
IP security (IPSec)
Used to secure communication, data streams in Internet environments (vpn external environments). This is the bottom line, the amount of traffic via IPSec is used mainly by Transport modes, or tunnels (or tunnels – this concept is often used in Proxy, SOCKS) to encrypt data in VPN.
L2TP

The L2TP protocol usually works with IPSec encryption algorithms. It is significantly stronger than PPTP but still worries users. The main vulnerability in L2TP/IPSec is the public key exchange method. The Diffie-Hellman public key exchange is a way for the two parties to agree on the next encryption key, and no one knows about it. There is a method that can “jailbreak” this process, which requires quite a large computing power, but then it allows access to all communication on a given VPN.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
There is a similar section to IPSec, the two protocols above also use passwords to ensure safety between connections in the Internet environment.
In addition, the two protocols also use Handshake mode – which is related to the account authentication process between the client and the server. In order for a connection to be considered successful, this authentication process will use certificates – the account authentication keys are stored on both the server and the client.
Protocols with better security
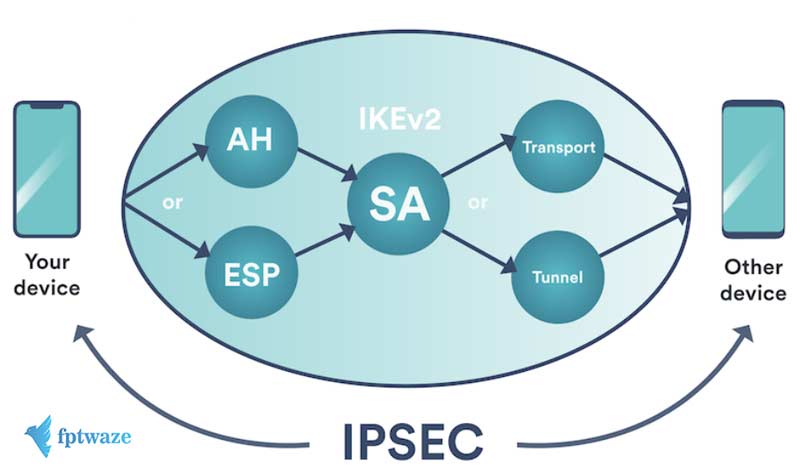
IKEv2 (Internet Key Exchange)
IKEv2 (Internet Key Exchange) is rated highly security among current protocols. IKEv2 uses IPSec tunnelling and has a wide selection of encryption protocols. IKEv2 is used with AES-256 encryption so it is difficult to crack. IKEv2 uses powerful certificate-based authentication and can use the HMAC algorithm to verify the integrity of the data transmitted. IKEv2 supports fast and especially powerful communication in maintaining sessions, even when the Internet connection is interrupted. Windows, MacOS, iOS, and Android all support IKEv2. Some open source implementations are also available.
Version 1 of the protocol was introduced in 1998 and version 2 in 2005. IKEv2 is not one of the latest protocols, but is very well maintained.
SSTP (Secure Socket Tunneling Protocol)
SSTP (Secure Socket Tunneling Protocol) is a Microsoft product, supported mainly on Windows. When used with AES and SSL encryption, SSTP offers good security, theoretically. No SSTP vulnerabilities have been found at the moment but it is likely that a certain weakness persists.
A practical problem with SSTP is limited support on non-Windows systems.
OpenVPN
OpenVPN is an open set of protocols that offer powerful security features and have become very popular. OpenVPN was first released in 2001 under the GPL license. OpenVPN is open source, so vulnerability testing is guaranteed. OpenVPN’s encryption usually uses the OpenSSL library. OpenSSL supports many encryption algorithms, including AES.
There isn’t any support for OpenVPN at the operating system level, but many plans include their own OpenVPN clients.
Having the most security with a protocol requires administrators to handle it correctly. The OpenVPN community offers recommendations to enhance the security of OpenVPN.
SoftEther (Software Ethernet)
SoftEther (Software Ethernet) is a new name, first launched in 2014. Like OpenVPN, SoftEther also has open source. SoftEther supports the most powerful encryption protocols, including AES-256 and RSA 4096-bit. SoftEther offers greater communication speeds than most protocols, including OpenVPN, at a certain data rate. It does not support its own operating system but can be installed on many operating systems, including Windows, Mac, Android, iOS, Linux and Unix.
As a new protocol, SoftEther is not as supported as some other protocols. SoftEther doesn’t last long enough like OpenVPN, so users don’t have much time to test the weaknesses that may appear on this protocol. However, SoftEther is a heavyweight candidate for anyone who needs top-noted security quality.
So which protocol to choose?
The question “Which protocol is the safest?” is difficult to come up with an answer. IKEv2, OpenVPN, and SoftEther are all strong contenders. OpenVPN and SoftEther have the advantage of being open source. IKEv2 has open source implementations but also exclusive implementations. The main security advantage of IKEv2 is its ease of installation, reducing the risk of configuration errors. SoftEther offers very good security, but users do not have as much time to experience SoftEther as with the other two protocols, so it is very likely that SoftEther still has problems that users have not discovered.
OpenVPN’s code has been in place for years for security experts to test. OpenVPN is widely used and supports the strongest encryption protocols. Final decision-making also needs to consider other factors, such as convenience and speed, or whether security is of greatest concern.
Advantages and Disadvantages of VPN
The theory is that, when applied to reality, how vpn will have pros and cons. You are invited to continue discussions with Network Administrators.
To build a private network, a virtual personal network, using a VPN is an inexpensive solution. We can imagine this, the Internet environment is the main bridge and communication to transmit data, in terms of cost, it is completely reasonable compared to paying to establish a separate connection with high prices. Besides, it is not cheap to use software and hardware systems to support the account authentication process. Comparing the convenience that a VPN offers along with the cost of setting up your own system, it’s clear that a VPN is dominant.
But besides that, there are very noticeable disadvantages such as:
VPN do not have the ability to manage Quality of Service (QoS) over the Internet, so data packages – Data packages are still at risk of being lost and risky. The management ability of VPN providers is limited, no one can expect what can happen to their customers, or in short, get hacked.